ADVERTISEMENT
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
the 70 days of treason... from the election to the inauguration...
- Thread starter WVU82
- Start date
https://themarketswork.com/2017/04/04/the-suspicious-timing-of-obamas-nsa-data-sharing-order/
The Suspicious Timing of Obama’s NSA Data-Sharing Order
April 4, 2017 by Jeff Carlson, CFA
On January 3, 2017, Section 2.3 of Executive Order 12333 – Procedures for the Availability or Dissemination of Raw Signals Intelligence Information by the NSA – was signed into effect. According to the New York Times:
“The new rules significantly relax longstanding limits on what the N.S.A. may do with the information gathered by its most powerful surveillance operations, which are largely unregulated by American wiretapping laws. These include collecting satellite transmissions, phone calls and emails that cross network switches abroad, and messages between people abroad that cross domestic network switches.”
Like many, I wondered at the timing of the order and possible ulterior motives on the part of the Obama White House. Why the pressing need to rush this order during the final days of his office? An order which allowed for significant expansion in the sharing of raw intelligence amongst agencies. Was it to enable dissemination of information gathered by those in the Obama Administration amongst intelligence agencies? But if so, why was the order not put into place earlier? Why just weeks before Trump officially assumed the Presidency?
In some ways, what I found particularly curious about this significant order is that it was so overdue. It had been expected to be put into place in early 2016 as reported by the NYT and many other sources. The order was reported as being on “the verge” of being finalized in late February of 2016. Why was the order delayed – and what was changed between that draft and the finalized version that was passed in the last weeks of the Obama Administration? Perhaps there was an innocent reason for the unexpected delays and/or revisions but the timing seemed suspect.
Upon closer examination, it was the restrictions placed within the new order that raised some flags – especially in light of recent events.
By May 2016 it was certain Trump would secure the GOP nomination – and it was seen as probable in late February 2016.
Reports of surveillance and unmasking of members of the Trump Camp are said to go back as much as one year – prior to President Trump securing the GOP nomination.
Section 2.3 of Executive Order 12333 was reported as being in the final stages of completion in late February 2016. Yet the order was not formally issued until January 3, 2017.
Now, examine the following language contained within the order Section 2.3 of Executive Order 12333 – Procedures for the Availability or Dissemination of Raw Signals Intelligence Information by the NSA on page 9 of the viewable document and page 6 of the actual document numbering under “General Protections”:
3. (U) Political Process in the United States. [Any IC element that obtains access to raw SIGINT under these Procedures will] Not engage in any intelligence activity authorized by these Procedures, including disseminations to the White House, for the purpose of affecting the political process in the United States. The IC element will comply with the guidance applicable to NSA regarding the application of this prohibition. Questions about whether a particular activity falls within this prohibition will be resolved in consultation with the element’s legal counsel and the General Counsel of the Office of the Director of National Intelligence (ODNI) (and the DoD’s Office of the General Counsel in the case of a DoD IC element).
And page 10 of the viewable document and page 7 of the actual document numbering under “Processing Raw SIGINT”:
2. (U) Other targets. Unless authorized under paragraph 1, foreign communications reasonably likely to be to, from, or about a U.S. person or a person located in the United States may not be intentionally selected for the purpose of targeting a U.S. person or a person in the United States, unless approved by:
a. (U) The Attorney General, if all of the following requirements are met:
(i) – Redacted – Blacked Out
(ii) (U) The person is an agent of a foreign power or an officer or employee of a foreign power; and
(iii) (U) The purpose of the selection is to acquire significant foreign intelligence or counterintelligence information.
And page 14 of the viewable document and page 11 of the actual document numbering under “Retention”:
D. (U) Communications between U.S. persons. Communications solely between U.S. persons inadvertently retrieved during the selection of foreign communications will be destroyed upon recognition, except:
1. (U) When the communication contains significant foreign intelligence or counterintelligence, the head of the recipient IC element may waive the destruction requirement and subsequently notify the DIRNSA and NSA’s OGC;
And page 14 of the viewable document and page 11 of the actual document numbering under “Dissemination”:
B. (U) Criteria for dissemination of USPI [U.S. Person Information]. Subject to paragraph A and to paragraphs C, D, and E below, an IC element may disseminate USPI derived solely from raw SIGINT covered by these Procedures only if one of the following conditions is met, and if a high-level official as specified in the MOA determines that the recipient has a need for the USPI in the performance of his or her official duties:
1. (U) Consent. The U.S. person has consented to the dissemination of (i) communications to, from, or about him or her, (ii) data related to such communications, or (iii) information about him or her, and has executed an appropriate consent form.
2. (U) Publicly available. The USPI is publicly available information.
3. (U) Understanding foreign intelligence or counterintelligence. The USPI is necessary to understand the foreign intelligence or counterintelligence information or assess its importance.
Note that under the new January 3, 2017 order, inter-agency sharing of information is easier and much broader. Agencies and individuals can ask the NSA for access to specific surveillance simply by claiming the intercepts contain relevant information that is useful to a particular mission. No privacy protection of the raw data occurs. Prior to these changes, the NSA filtered information before sharing intercepted communications with another agency. Under the new rules, sharing of information has been made significantly easier – and the information shared is raw and unfiltered.
But – it appears that there are some significant – and new – protections placed into the January 3, 2017 order covering the specific manner in which information may be used, disseminated, collected – and destroyed. Notably, the first portion I listed; Section 3 – Political Process in the United States under General Protections, specifically prohibits disseminations to the White House for political purposes. Some of the other restrictions listed seem to apply as well.
This language appears to be new – as far as I can tell it did not exist in the older 12333 regulations. Which might explain the lengthy delay in Section 2.3’s formal implementation.
If this language had been implemented in early 2016 when originally scheduled, the requests for unmasking of names may have been significantly less likely to be granted. It’s quite possible the new language could have completely prohibited any unmasking of members of Trump’s Campaign, Transition Team or associates – due to the political nature of those individuals – at least as far as the White House was concerned. At a minimum, the legal bar for the unmasking of politically-related individuals appears to have been moved much higher under the new order.
Prior to the formal signing of Section 2.3 it appears that there existed more latitude within the White House in regards to collection of information on the Trump Campaign. However, once signed into effect, Section 2.3 granted broad latitude in regards to inter-agency sharing of information. By the time the new order was signed, the information was already in the Obama White House’s possession.
It appears to me that these new restrictions – and/or clarifications of older restrictions – contained within the new order, might have limited the ability of Susan Rice or others to act legally in requesting or granting the unmasking of names relating to political opponents if the order had been enacted earlier. The new order, had it been implemented earlier, might have restricted White House access to information regarding the Trump Team in any form.The same would seem to apply to surveillance of those same individuals.
The timing and formal implementation of “Procedures for the Availability or Dissemination of Raw Signals Intelligence Information By The National Security Agency Under Section 2.3 of Executive Order 12333” seems all the more suspicious to me now that I have taken a closer look at its provisions.
And in light of the unmaskings.
The Suspicious Timing of Obama’s NSA Data-Sharing Order
April 4, 2017 by Jeff Carlson, CFA
On January 3, 2017, Section 2.3 of Executive Order 12333 – Procedures for the Availability or Dissemination of Raw Signals Intelligence Information by the NSA – was signed into effect. According to the New York Times:
“The new rules significantly relax longstanding limits on what the N.S.A. may do with the information gathered by its most powerful surveillance operations, which are largely unregulated by American wiretapping laws. These include collecting satellite transmissions, phone calls and emails that cross network switches abroad, and messages between people abroad that cross domestic network switches.”
Like many, I wondered at the timing of the order and possible ulterior motives on the part of the Obama White House. Why the pressing need to rush this order during the final days of his office? An order which allowed for significant expansion in the sharing of raw intelligence amongst agencies. Was it to enable dissemination of information gathered by those in the Obama Administration amongst intelligence agencies? But if so, why was the order not put into place earlier? Why just weeks before Trump officially assumed the Presidency?
In some ways, what I found particularly curious about this significant order is that it was so overdue. It had been expected to be put into place in early 2016 as reported by the NYT and many other sources. The order was reported as being on “the verge” of being finalized in late February of 2016. Why was the order delayed – and what was changed between that draft and the finalized version that was passed in the last weeks of the Obama Administration? Perhaps there was an innocent reason for the unexpected delays and/or revisions but the timing seemed suspect.
Upon closer examination, it was the restrictions placed within the new order that raised some flags – especially in light of recent events.
By May 2016 it was certain Trump would secure the GOP nomination – and it was seen as probable in late February 2016.
Reports of surveillance and unmasking of members of the Trump Camp are said to go back as much as one year – prior to President Trump securing the GOP nomination.
Section 2.3 of Executive Order 12333 was reported as being in the final stages of completion in late February 2016. Yet the order was not formally issued until January 3, 2017.
Now, examine the following language contained within the order Section 2.3 of Executive Order 12333 – Procedures for the Availability or Dissemination of Raw Signals Intelligence Information by the NSA on page 9 of the viewable document and page 6 of the actual document numbering under “General Protections”:
3. (U) Political Process in the United States. [Any IC element that obtains access to raw SIGINT under these Procedures will] Not engage in any intelligence activity authorized by these Procedures, including disseminations to the White House, for the purpose of affecting the political process in the United States. The IC element will comply with the guidance applicable to NSA regarding the application of this prohibition. Questions about whether a particular activity falls within this prohibition will be resolved in consultation with the element’s legal counsel and the General Counsel of the Office of the Director of National Intelligence (ODNI) (and the DoD’s Office of the General Counsel in the case of a DoD IC element).
And page 10 of the viewable document and page 7 of the actual document numbering under “Processing Raw SIGINT”:
2. (U) Other targets. Unless authorized under paragraph 1, foreign communications reasonably likely to be to, from, or about a U.S. person or a person located in the United States may not be intentionally selected for the purpose of targeting a U.S. person or a person in the United States, unless approved by:
a. (U) The Attorney General, if all of the following requirements are met:
(i) – Redacted – Blacked Out
(ii) (U) The person is an agent of a foreign power or an officer or employee of a foreign power; and
(iii) (U) The purpose of the selection is to acquire significant foreign intelligence or counterintelligence information.
And page 14 of the viewable document and page 11 of the actual document numbering under “Retention”:
D. (U) Communications between U.S. persons. Communications solely between U.S. persons inadvertently retrieved during the selection of foreign communications will be destroyed upon recognition, except:
1. (U) When the communication contains significant foreign intelligence or counterintelligence, the head of the recipient IC element may waive the destruction requirement and subsequently notify the DIRNSA and NSA’s OGC;
And page 14 of the viewable document and page 11 of the actual document numbering under “Dissemination”:
B. (U) Criteria for dissemination of USPI [U.S. Person Information]. Subject to paragraph A and to paragraphs C, D, and E below, an IC element may disseminate USPI derived solely from raw SIGINT covered by these Procedures only if one of the following conditions is met, and if a high-level official as specified in the MOA determines that the recipient has a need for the USPI in the performance of his or her official duties:
1. (U) Consent. The U.S. person has consented to the dissemination of (i) communications to, from, or about him or her, (ii) data related to such communications, or (iii) information about him or her, and has executed an appropriate consent form.
2. (U) Publicly available. The USPI is publicly available information.
3. (U) Understanding foreign intelligence or counterintelligence. The USPI is necessary to understand the foreign intelligence or counterintelligence information or assess its importance.
Note that under the new January 3, 2017 order, inter-agency sharing of information is easier and much broader. Agencies and individuals can ask the NSA for access to specific surveillance simply by claiming the intercepts contain relevant information that is useful to a particular mission. No privacy protection of the raw data occurs. Prior to these changes, the NSA filtered information before sharing intercepted communications with another agency. Under the new rules, sharing of information has been made significantly easier – and the information shared is raw and unfiltered.
But – it appears that there are some significant – and new – protections placed into the January 3, 2017 order covering the specific manner in which information may be used, disseminated, collected – and destroyed. Notably, the first portion I listed; Section 3 – Political Process in the United States under General Protections, specifically prohibits disseminations to the White House for political purposes. Some of the other restrictions listed seem to apply as well.
This language appears to be new – as far as I can tell it did not exist in the older 12333 regulations. Which might explain the lengthy delay in Section 2.3’s formal implementation.
If this language had been implemented in early 2016 when originally scheduled, the requests for unmasking of names may have been significantly less likely to be granted. It’s quite possible the new language could have completely prohibited any unmasking of members of Trump’s Campaign, Transition Team or associates – due to the political nature of those individuals – at least as far as the White House was concerned. At a minimum, the legal bar for the unmasking of politically-related individuals appears to have been moved much higher under the new order.
Prior to the formal signing of Section 2.3 it appears that there existed more latitude within the White House in regards to collection of information on the Trump Campaign. However, once signed into effect, Section 2.3 granted broad latitude in regards to inter-agency sharing of information. By the time the new order was signed, the information was already in the Obama White House’s possession.
It appears to me that these new restrictions – and/or clarifications of older restrictions – contained within the new order, might have limited the ability of Susan Rice or others to act legally in requesting or granting the unmasking of names relating to political opponents if the order had been enacted earlier. The new order, had it been implemented earlier, might have restricted White House access to information regarding the Trump Team in any form.The same would seem to apply to surveillance of those same individuals.
The timing and formal implementation of “Procedures for the Availability or Dissemination of Raw Signals Intelligence Information By The National Security Agency Under Section 2.3 of Executive Order 12333” seems all the more suspicious to me now that I have taken a closer look at its provisions.
And in light of the unmaskings.
Congressman Brought a Bucket of Fried Chicken to Hearing ...
https://time.com/5581923/congressman-eating-fried-chicken-meme/
R ep. Steve Cohen may have been trying to make a joke when he arrived to a House Judiciary Committee hearing with fried chicken. But that doesn't mean he didn't enjoy his breakfast.. Ahead of ...
https://time.com/5581923/congressman-eating-fried-chicken-meme/
R ep. Steve Cohen may have been trying to make a joke when he arrived to a House Judiciary Committee hearing with fried chicken. But that doesn't mean he didn't enjoy his breakfast.. Ahead of ...
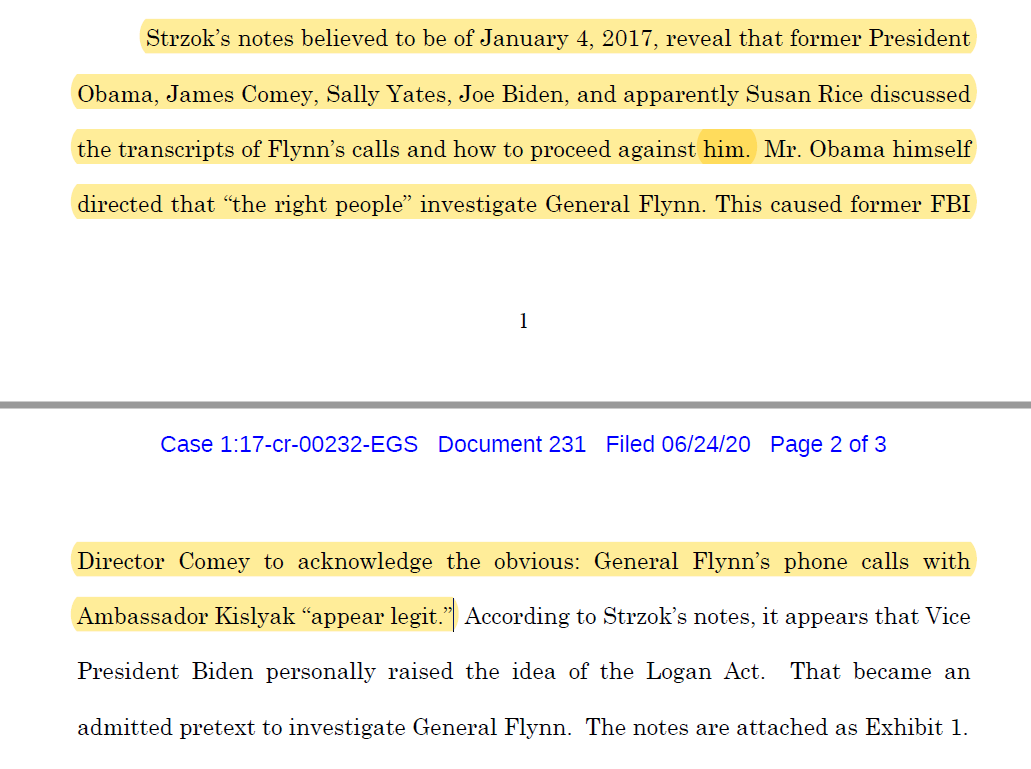
I think the bottom line on all of this rests in post #21 82 has provided here. Obama knew about all of this! It may be hard to factually prove he orchestrated it (my personal belief) but no way the evidence suggests he wasn't intimately aware of exactly what was going on with Flynn, the FISA court, the illegal unmasking, illegal surveillance...ALL OF IT!
To me, it's just sheer media incompetence, intransigence, or outright corruption they aren't asking the two most obvious questions right now: what did Obama know, and when did he know it? They won't ask those questions because they already know the answer!
He knew about all of it from the very beginning! Let's see if the prospect of jail time for Comey, Clapper, Lynch et all doesn't convince one of them to turn on Zero like they all tried to get Flynn to turn on Trump?
Leftists have no loyalty.
Hey atl, if I go down I'm sure taking all of them with me!

To me, it's just sheer media incompetence, intransigence, or outright corruption they aren't asking the two most obvious questions right now: what did Obama know, and when did he know it? They won't ask those questions because they already know the answer!
He knew about all of it from the very beginning! Let's see if the prospect of jail time for Comey, Clapper, Lynch et all doesn't convince one of them to turn on Zero like they all tried to get Flynn to turn on Trump?
Leftists have no loyalty.
Hey atl, if I go down I'm sure taking all of them with me!

Last edited:
Hey @WVUBRU this is from direct testimony under oath to the House intel committee based on their recently released full transcripts. This is the official legal and factual record.
Do you now accept this as the definitive factual proof there was no "collusion" on the part of the Trump campaign or administration with the Russians?

If you don't answer me, then I have proof you lied when YOU said you always accept facts when presented to you. Was that a lie, or is it this "collusion" story you still believe in?
Do you now accept this as the definitive factual proof there was no "collusion" on the part of the Trump campaign or administration with the Russians?

If you don't answer me, then I have proof you lied when YOU said you always accept facts when presented to you. Was that a lie, or is it this "collusion" story you still believe in?
Helluva job, 82. I don’t visit this board often, so I just discovered this thread. Reading it all at once, and for the very first time, made for dramatic effect. Nearly a one year buildup just in this thread! Going through this, a reader can really see the momentum building for Flynn and the layers of the onion gradually peeling off to the rotten core. Tremendous compilation.
https://obamawhitehouse.archives.go...response-russian-malicious-cyber-activity-and
For Immediate Release
December 29, 2016
FACT SHEET: Actions in Response to Russian Malicious Cyber Activity and Harassment
Today, President Obama authorized a number of actions in response to the Russian government’s aggressive harassment of U.S. officials and cyber operations aimed at the U.S. election in 2016. Russia’s cyber activities were intended to influence the election, erode faith in U.S. democratic institutions, sow doubt about the integrity of our electoral process, and undermine confidence in the institutions of the U.S. government. These actions are unacceptable and will not be tolerated.
Sanctioning Malicious Russian Cyber Activity
In response to the threat to U.S. national security posed by Russian interference in our elections, the President has approved an amendment to Executive Order 13964. As originally issued in April 2015, this Executive Order created a new, targeted authority for the U.S. government to respond more effectively to the most significant of cyber threats, particularly in situations where malicious cyber actors operate beyond the reach of existing authorities. The original Executive Order focused on cyber-enabled malicious activities that:
Over the past two years, harassment of our diplomatic personnel in Russia by security personnel and police has increased significantly and gone far beyond international diplomatic norms of behavior. Other Western Embassies have reported similar concerns. In response to this harassment, the President has authorized the following actions:
The Department of Homeland Security and Federal Bureau of Investigation are releasing a Joint Analysis Report (JAR) that contains declassified technical information on Russian civilian and military intelligence services’ malicious cyber activity, to better help network defenders in the United States and abroad identify, detect, and disrupt Russia’s global campaign of malicious cyber activities.
Cyber threats pose one of the most serious economic and national security challenges the United States faces today. For the last eight years, this Administration has pursued a comprehensive strategy to confront these threats. And as we have demonstrated by these actions today, we intend to continue to employ the full range of authorities and tools, including diplomatic engagement, trade policy tools, and law enforcement mechanisms, to counter the threat posed by malicious cyber actors, regardless of their country of origin, to protect the national security of the United States.
For Immediate Release
December 29, 2016
FACT SHEET: Actions in Response to Russian Malicious Cyber Activity and Harassment
Today, President Obama authorized a number of actions in response to the Russian government’s aggressive harassment of U.S. officials and cyber operations aimed at the U.S. election in 2016. Russia’s cyber activities were intended to influence the election, erode faith in U.S. democratic institutions, sow doubt about the integrity of our electoral process, and undermine confidence in the institutions of the U.S. government. These actions are unacceptable and will not be tolerated.
Sanctioning Malicious Russian Cyber Activity
In response to the threat to U.S. national security posed by Russian interference in our elections, the President has approved an amendment to Executive Order 13964. As originally issued in April 2015, this Executive Order created a new, targeted authority for the U.S. government to respond more effectively to the most significant of cyber threats, particularly in situations where malicious cyber actors operate beyond the reach of existing authorities. The original Executive Order focused on cyber-enabled malicious activities that:
- Harm or significantly compromise the provision of services by entities in a critical infrastructure sector;
- Significantly disrupt the availability of a computer or network of computers (for example, through a distributed denial-of-service attack); or
- Cause a significant misappropriation of funds or economic resources, trade secrets, personal identifiers, or financial information for commercial or competitive advantage or private financial gain (for example, by stealing large quantities of credit card information, trade secrets, or sensitive information).
- Tamper with, alter, or cause a misappropriation of information with the purpose or effect of interfering with or undermining election processes or institutions.
- The Main Intelligence Directorate (a.k.a. Glavnoe Razvedyvatel’noe Upravlenie) (a.k.a. GRU) is involved in external collection using human intelligence officers and a variety of technical tools, and is designated for tampering, altering, or causing a misappropriation of information with the purpose or effect of interfering with the 2016 U.S. election processes.
- The Federal Security Service (a.k.a. Federalnaya Sluzhba Bezopasnosti) (a.k.a FSB) assisted the GRU in conducting the activities described above.
- The three other entities include the Special Technology Center (a.k.a. STLC, Ltd. Special Technology Center St. Petersburg) assisted the GRU in conducting signals intelligence operations; Zorsecurity (a.k.a. Esage Lab) provided the GRU with technical research and development; and the Autonomous Noncommercial Organization “Professional Association of Designers of Data Processing Systems” (a.k.a. ANO PO KSI) provided specialized training to the GRU.
- Sanctioned individuals include Igor Valentinovich Korobov, the current Chief of the GRU; Sergey Aleksandrovich Gizunov, Deputy Chief of the GRU; Igor Olegovich Kostyukov, a First Deputy Chief of the GRU; and Vladimir Stepanovich Alexseyev, also a First Deputy Chief of the GRU.
- Evgeniy Mikhailovich Bogachev is designated today for having engaged in significant malicious cyber-enabled misappropriation of financial information for private financial gain. Bogachev and his cybercriminal associates are responsible for the theft of over $100 million from U.S. financial institutions, Fortune 500 firms, universities, and government agencies.
- Aleksey Alekseyevich Belan engaged in the significant malicious cyber-enabled misappropriation of personal identifiers for private financial gain. Belan compromised the computer networks of at least three major United States-based e-commerce companies.
Over the past two years, harassment of our diplomatic personnel in Russia by security personnel and police has increased significantly and gone far beyond international diplomatic norms of behavior. Other Western Embassies have reported similar concerns. In response to this harassment, the President has authorized the following actions:
- Today the State Department declared 35 Russian government officials from the Russian Embassy in Washington and the Russian Consulate in San Francisco “persona non grata.” They were acting in a manner inconsistent with their diplomatic status. Those individuals and their families were given 72 hours to leave the United States.
- In addition to this action, the Department of State has provided notice that as of noon on Friday, December 30, Russian access will be denied to two Russian government-owned compounds, one in Maryland and one in New York.
The Department of Homeland Security and Federal Bureau of Investigation are releasing a Joint Analysis Report (JAR) that contains declassified technical information on Russian civilian and military intelligence services’ malicious cyber activity, to better help network defenders in the United States and abroad identify, detect, and disrupt Russia’s global campaign of malicious cyber activities.
- The JAR includes information on computers around the world that Russian intelligence services have co-opted without the knowledge of their owners in order to conduct their malicious activity in a way that makes it difficult to trace back to Russia. In some cases, the cybersecurity community was aware of this infrastructure, in other cases, this information is newly declassified by the U.S. government.
- The report also includes data that enables cybersecurity firms and other network defenders to identify certain malware that the Russian intelligence services use. Network defenders can use this information to identify and block Russian malware, forcing the Russian intelligence services to re-engineer their malware. This information is newly de-classified.
- Finally, the JAR includes information on how Russian intelligence services typically conduct their activities. This information can help network defenders better identify new tactics or techniques that a malicious actor might deploy or detect and disrupt an ongoing intrusion.
Cyber threats pose one of the most serious economic and national security challenges the United States faces today. For the last eight years, this Administration has pursued a comprehensive strategy to confront these threats. And as we have demonstrated by these actions today, we intend to continue to employ the full range of authorities and tools, including diplomatic engagement, trade policy tools, and law enforcement mechanisms, to counter the threat posed by malicious cyber actors, regardless of their country of origin, to protect the national security of the United States.
Durham well aware of these dirtbags, .......... interesting times ahead.
Similar threads
- Replies
- 3
- Views
- 138
- Replies
- 2
- Views
- 170
- Replies
- 4
- Views
- 327
ADVERTISEMENT
ADVERTISEMENT